Social engineering attacks are determined by psychological manipulation and deception and should be released via different conversation channels, together with electronic mail, text, telephone or social media. The target of such a attack is to locate a route in the Group to extend and compromise the electronic attack surface.
It refers to each of the likely ways an attacker can connect with a procedure or network, exploit vulnerabilities, and acquire unauthorized obtain.
This at any time-evolving danger landscape necessitates that corporations create a dynamic, ongoing cybersecurity method to remain resilient and adapt to emerging risks.
Considering the fact that these attempts are sometimes led by IT groups, instead of cybersecurity industry experts, it’s important to ensure that information and facts is shared across Just about every functionality and that every one group members are aligned on security operations.
Furthermore, vulnerabilities in processes made to avert unauthorized use of an organization are thought of Portion of the physical attack surface. This may include things like on-premises security, such as cameras, security guards, and fob or card techniques, or off-premise safeguards, such as password suggestions and two-factor authentication protocols. The Bodily attack surface also consists of vulnerabilities related to Bodily gadgets like routers, servers along with other hardware. If this type of attack is profitable, the next phase is often to develop the attack on the electronic attack surface.
Businesses can evaluate opportunity vulnerabilities by identifying the physical and Digital products that comprise their attack surface, which often can include company firewalls and switches, network file servers, personal computers and laptops, cellular products, and printers.
Management accessibility. Corporations should limit entry to sensitive info and methods both of those internally and externally. They could use Actual physical steps, for example locking access cards, biometric programs and multifactor authentication.
Attack surface administration requires businesses to assess their pitfalls and put into action security actions and controls to shield by themselves as A part of an In general hazard mitigation system. Key queries answered in attack surface management consist of the subsequent:
These structured criminal groups deploy ransomware to extort organizations for money get. They are usually primary subtle, Company Cyber Ratings multistage fingers-on-keyboard attacks that steal data and disrupt business enterprise functions, demanding significant ransom payments in exchange for decryption keys.
Weak passwords (such as 123456!) or stolen sets allow for a Artistic hacker to get easy access. The moment they’re in, They might go undetected for some time and do a good deal of injury.
Empower collaboration: RiskIQ Illuminate permits business security teams to seamlessly collaborate on risk investigations or incident reaction engagements by overlaying interior knowledge and danger intelligence on analyst benefits.
Frequent attack surface vulnerabilities Widespread vulnerabilities involve any weak issue in the network that may end up in a data breach. This contains gadgets, for example personal computers, cell phones, and hard drives, together with buyers on their own leaking knowledge to hackers. Other vulnerabilities contain using weak passwords, a lack of e mail security, open ports, along with a failure to patch software program, which provides an open backdoor for attackers to target and exploit people and organizations.
Corporations’ attack surfaces are frequently evolving and, in doing so, usually grow to be additional complex and challenging to shield from threat actors. But detection and mitigation endeavours ought to preserve rate Together with the evolution of cyberattacks. What is actually a lot more, compliance continues to become progressively vital, and companies viewed as at large danger of cyberattacks generally spend increased insurance rates.
Zero have confidence in is usually a cybersecurity system in which each and every person is verified and every connection is approved. No-one is offered usage of means by default.
 Shaun Weiss Then & Now!
Shaun Weiss Then & Now! Barret Oliver Then & Now!
Barret Oliver Then & Now! Devin Ratray Then & Now!
Devin Ratray Then & Now!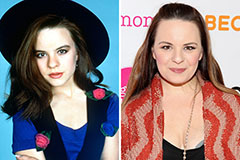 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now! Bill Cosby Then & Now!
Bill Cosby Then & Now!